The Information Security Risk Assessment and Treatment feature in CIMSNex allows users to assess and address risks associated with information assets based on the ISO 27005 methodology.
To complete the Information Security Risk Assessment (ISRA) based on the ISO 27005 methodology, Navigate to the "Planning" menu and hover over "Infosec Risk Assessment." Click on "Infosec Risk Assessment" to initiate a new assessment. A list of information assets will be displayed. Click the "Add" button next to the asset you want to assess and complere the fields as below.-
ISRA ID: Unique identifier for the Information Security Risk Assessment.
-
Date: Date when the assessment is conducted.
-
Vulnerability: Select the vulnerability associated with the asset.
-
Risk: Select the risk due to the asset vulnerability
-
Risk Impact: Slect the impact rating of the risk
-
Risk Likelihood: Select the likelihood rating of the risk occurring.
-
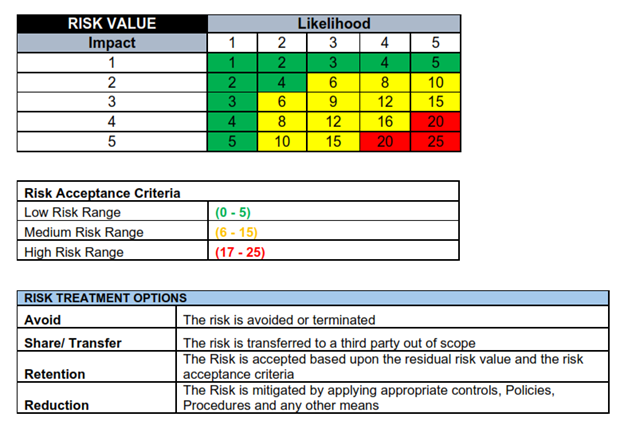
Risk Rating: Calculated by the system based on the criteria below.
-
Risk Ranking: System assigned priority to the risk based on the criteria below.
-
Risk Owner: Input the responsible individual or department.
-
Risk Treatment: Choose a treatment option (Avoid, Retain, Reduce, Transfer/Share).
-
Reason for Retaining: Provide justification if retaining the risk.
-
Additional Description: Include any relevant details or comments.
-
Organizational Control - Select the applicable organisational control reference
-
People Control - Select the applicable People control reference
-
Physical Control - Select the applicable Physical control reference
-
Technological Control - Select the applicable Technological control reference
-
Attachment: Attach relevant files or documents.
-
Additional Details: Provide any further information or observations.
After submitting the assessment, the Risk Register will be generated with additional fields included to provide detailed information related to the threat that will expose the vulnerability and specific control references for each of the four control categories: Organizational Control Ref, People Control Ref, Physical Control Ref, and Technological Control Ref.
This Risk Register will serve as input to the Risk Treatment Planning feature, which constitutes the next step in the risk management process.
RISK ASSESSMENT CRITERIA
RISK TREATMENT PLANNING
The next feature is Infosec Risk Treatment Planning, conducted after the risk assessment to strategize the treatment of identified risks through the implementation of controls, such as policies and other measures. To create a risk treatment plan, follow these steps:
Navigate to the "Planning" menu. Hover over "Infosec Risk Assessment & Treatment" and click on "Infosec Risk Treatment Planning". Complete the form by selecting additional controls from the Control Reference dropdown as below
-
RTP ID: This is a unique identifier for the Risk Treatment Plan (RTP) being prepared. It helps track and reference the plan when needed.
-
Date: Specify the date when the risk treatment plan is being created or documented.
-
Control Reference: Select a control of your choice to apply inthe treatment of the risk.
-
People Control Action Plan: Specify the actions or steps to be taken regarding people-related controls to mitigate or transfer/share the identified risks. This can involve training programs, awareness campaigns, access control enhancements, or any other measures involving human factors.
-
AssignedTo: Identify the individual or department responsible for executing the risk treatment plan. This can be a specific role within the organization or a designated team responsible for overseeing the plan's implementation.
-
Deadline: Set a deadline for completing the risk treatment plan. This helps establish a timeframe for implementing the necessary actions and monitoring progress.
- Frequency: If it is an ongoign action plan, select appropriate option
Verification of Risk Treatment Plans:
To verify the action plan, Navigate to the "Planning" menu, Hover over "Infosec Risk Assessment & Treatment" and click on "Infosec Risk Treatment Verification". A list of planned activities will be displayed and Select each activity one by one and click the "Verify" button
-
Verification Status: Indicate the status of the verification process for the risk treatment plans.
-
Completion Date: Specify the date when the verification process for the risk treatment plans was completed. This helps establish a timeline for assessing the effectiveness of the implemented measures.
-
Completed by: Identify the individual or team responsible for conducting the verification process. This field helps attribute accountability for the verification activities.
-
Comment/Lesson Learnt: Provide any relevant comments or lessons learned during the verification process. This can include observations, feedback, or insights gained from evaluating the effectiveness of the risk treatment plans.
-
Training or Awareness Done: Specify whether any additional training or awareness initiatives were conducted as part of the verification process. This field helps assess the overall level of knowledge and preparedness within the organization.
-
Attachment: If applicable, include any supporting documents or evidence related to the verification process. This can include reports, assessment findings, or other relevant materials.
The list will not clear, allowing you to come back and reverify periodically as part of the review process.
RISK TREATMENT PLAN
To check the Risk Treatment Plan:
- Navigate to the "Planning" menu.
- Hover over "Infosec Risk Assessment & Treatment" and click on "View Risk Treatment Plan".
- View all plans and their status of implementation in the generated report.




